Deploying Casdoor
There are several types of Single Sign-On (SSO) authentication sources (protocols):
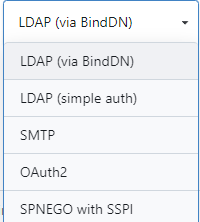
The mainstream protocols are LDAP, SMTP, OAuth2.0, etc., with OAuth2.0 being the most popular. There are numerous platforms in the open-source community that support OAuth, such as Keycloak, Okta, Casdoor, as well as many third-party OAuth2 Server SDKs or commercial paid platforms. After a selection process, it was decided to use Casdoor as the single sign-on authentication center.
Official website:
https://casdoor.org/zh/docs/overview
Casdoor is a user-interface-first Identity Access Management (IAM)/Single Sign-On (SSO) platform. Its web UI supports OAuth 2.0, OIDC, SAML, CAS, LDAP, SCIM, WebAuthn, TOTP, MFA, RADIUS, Google Workspace, Active Directory, and Kerberos.
The official documentation introduces the features of Casdoor. Casdoor supports multiple languages, is easy to deploy, has a simple and convenient interface, is powerful and comprehensive in functionality, and supports integration with various external login platforms such as Feishu. Therefore, I chose Casdoor.
Casdoor relies on a database, and you need to create a database first. It supports MySQL, PostgreSQL, and SQLite. You need to create a database named casdoor in advance.
Next, create an empty directory and create an app.conf file with the following sample content:
appname = casdoor
httpport = 8000
runmode = dev
SessionOn = true
copyrequestbody = true
driverName = mysql
dataSourceName = root:123456@tcp(localhost:3306)/
dbName = casdoor
tableNamePrefix =
showSql = false
redisEndpoint =
defaultStorageProvider =
isCloudIntranet = false
authState = "casdoor"
socks5Proxy = "127.0.0.1:10808"
verificationCodeTimeout = 10
initScore = 2000
logPostOnly = true
origin = "https://door.casdoor.com"
staticBaseUrl = "https://cdn.casbin.org"
enableGzip = true
inactiveTimeoutMinutes =
The key part to replace is the dataSourceName database connection string, which varies by database type. Please refer to:
https://casdoor.org/zh/docs/basic/server-installation/#%E9%85%8D%E7%BD%AE%E6%95%B0%E6%8D%AE%E5%BA%93
Then modify the origin to the address of the deployed service's open page, although it can also be left unchanged and modified later.
To deploy Casdoor using Docker:
docker run -p 8000:8000 -v /data/casdoor/conf:/conf casbin/casdoor:latest
Open the page through reverse proxy. The default username and password are admin, 123.
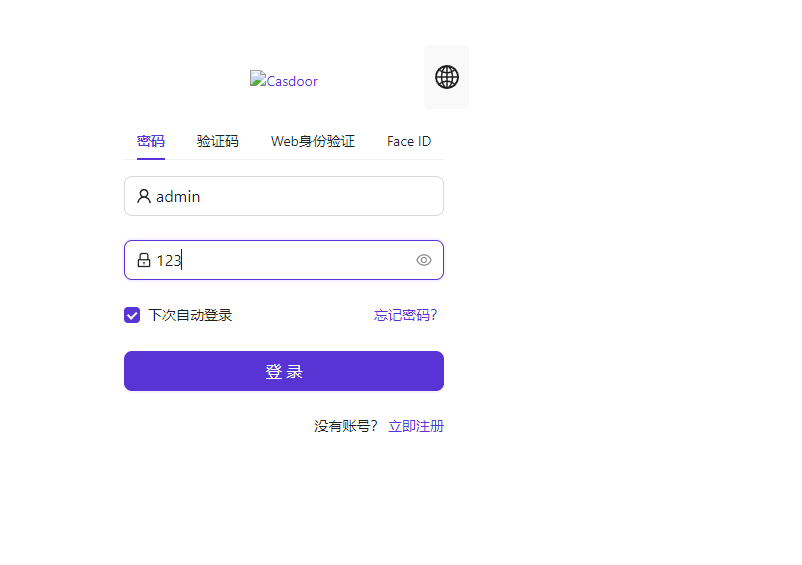
Configuring Casdoor
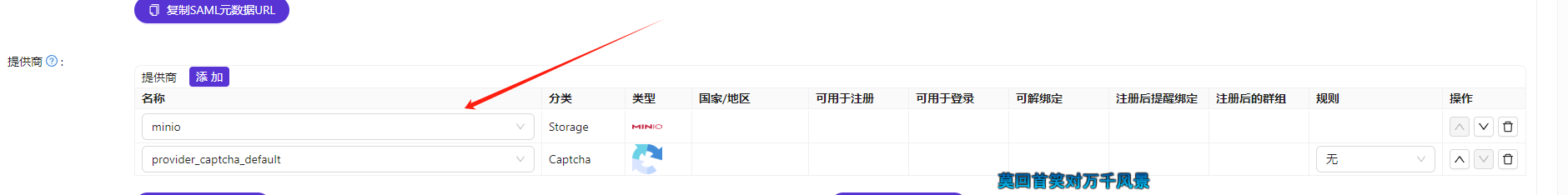
After logging in, create an object storage provider to persistently store some profile pictures and other static resources.
I am using a privately deployed Minio.
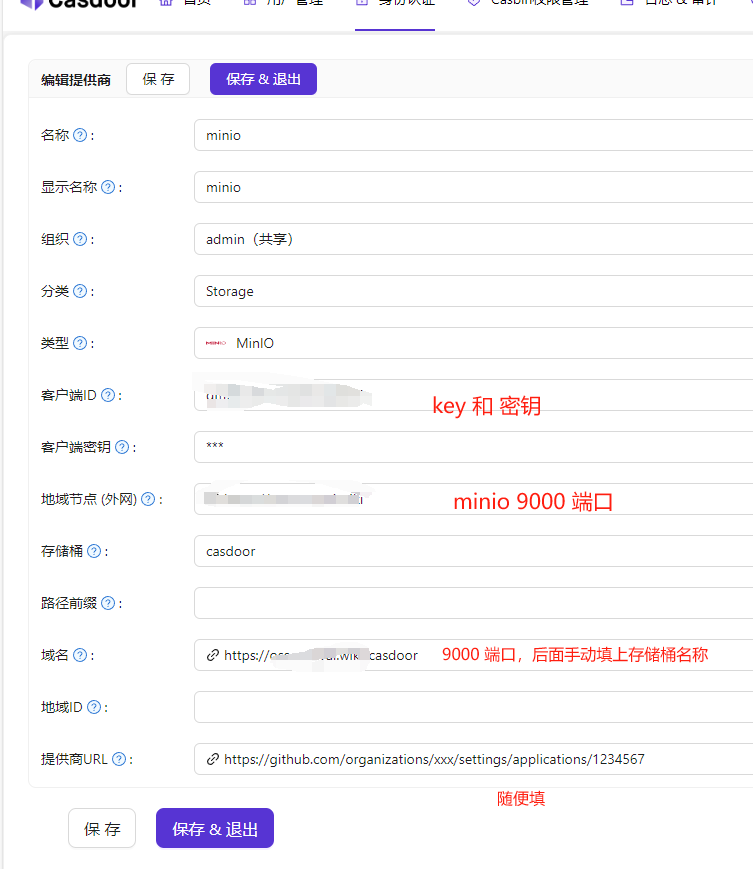
Then open the default application.
Add Minio storage in the provider settings.
Subsequently, uploaded images and files will automatically be stored in Minio and served as static resources for access.
Binding Gitea and Casdoor
Casdoor, as a single sign-on center, can integrate with any client that supports OAuth2.0. Here, I will explain how to connect Casdoor with Gitea for authentication.
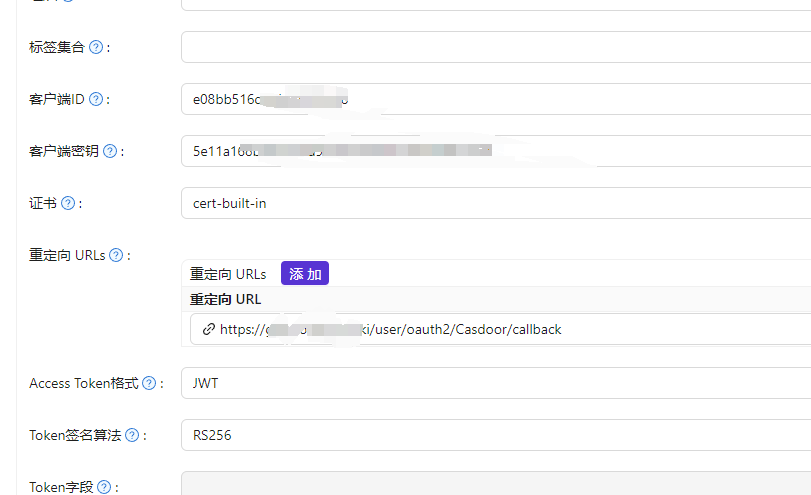
Manually open Casdoor and add an application. You only need to fill in the following information, and the redirect URL can be filled in arbitrarily, starting with the default value. Then copy the Client ID and secret.
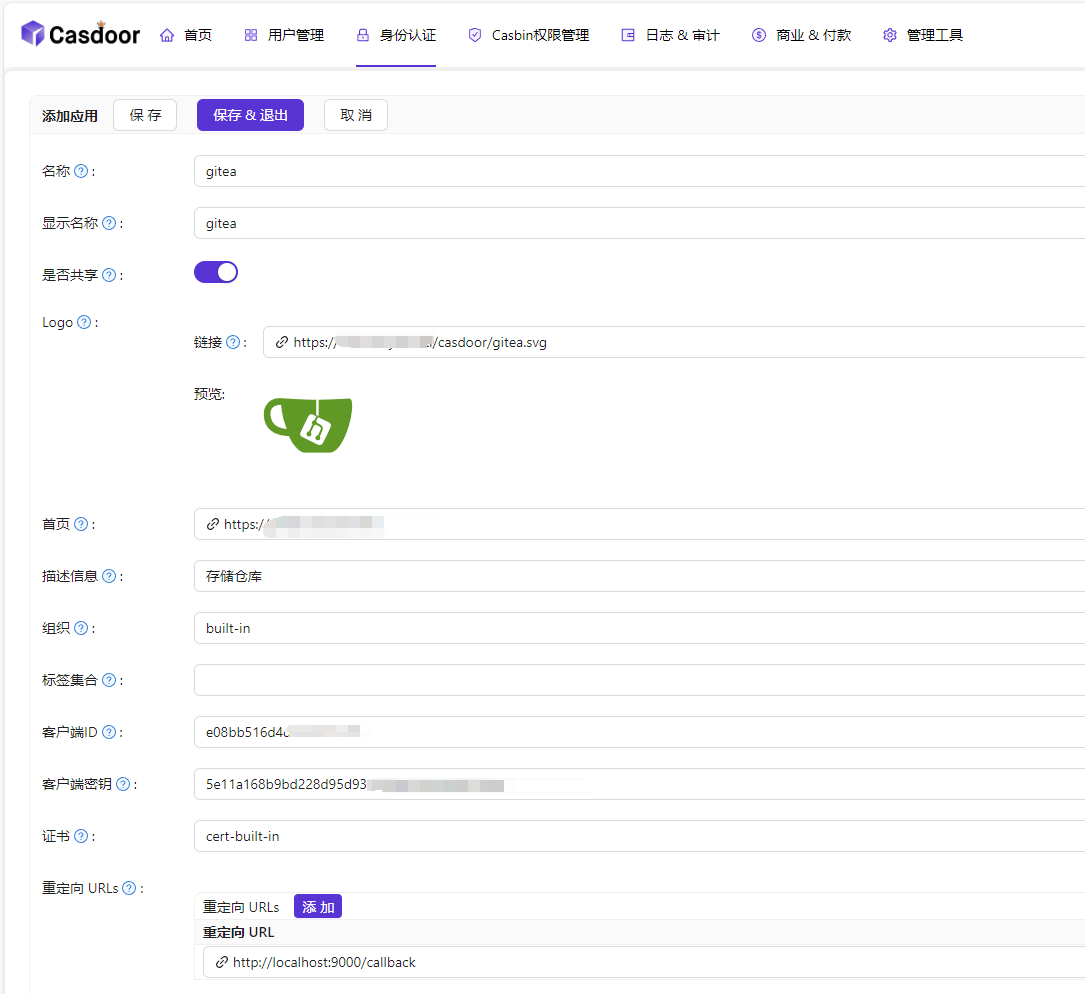
Then open Gitea and add the authentication source in the admin backend.
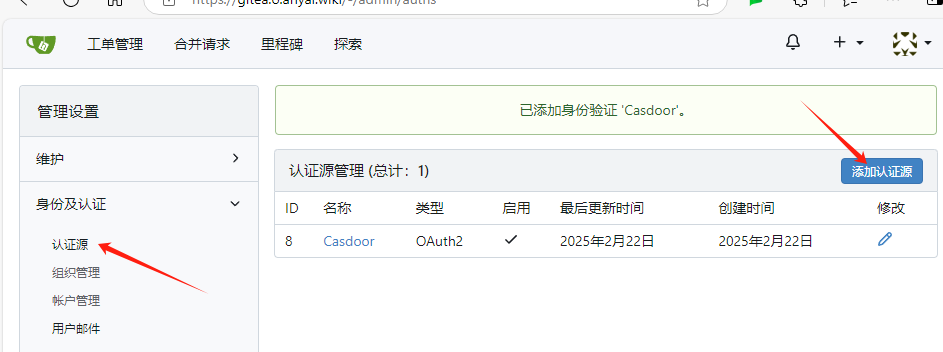
For OAuth2.0, different types of platforms have different endpoints, with Casdoor corresponding to OpenID Connect.
| Endpoint | URL |
| -------------------------- | --------------------------------- |
| OpenID Connect Discovery | /.well-known/openid-configuration |
| Authorization Endpoint | /login/oauth/authorize |
| Access Token Endpoint | /login/oauth/access_token |
| OpenID Connect UserInfo | /login/oauth/userinfo |
| JSON Web Key Set | /login/oauth/keys |
When filling in the OpenID Connect discovery URL, you need to add `/.well-known/openid-configuration` to the Casdoor access URL.
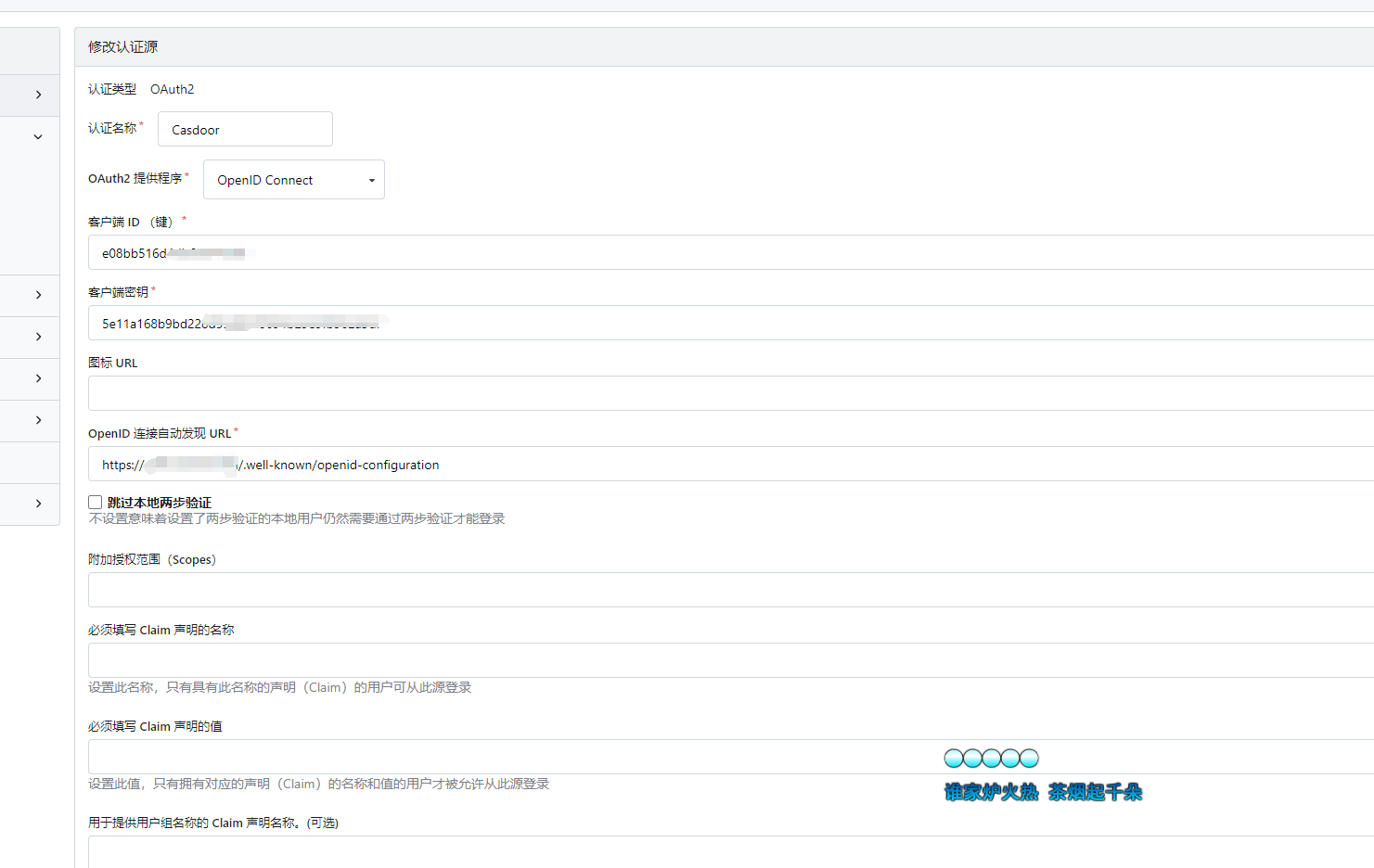
After saving the connection source, reopen that link source and find the callback URL generated by Gitea at the bottom.
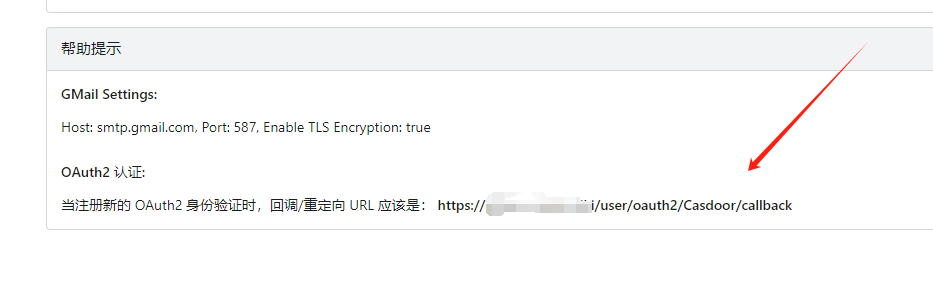
Reopen Casdoor and modify the callback URL in the Gitea application:
Log out of Gitea and log back in. The interface will display "Log in with Casdoor."
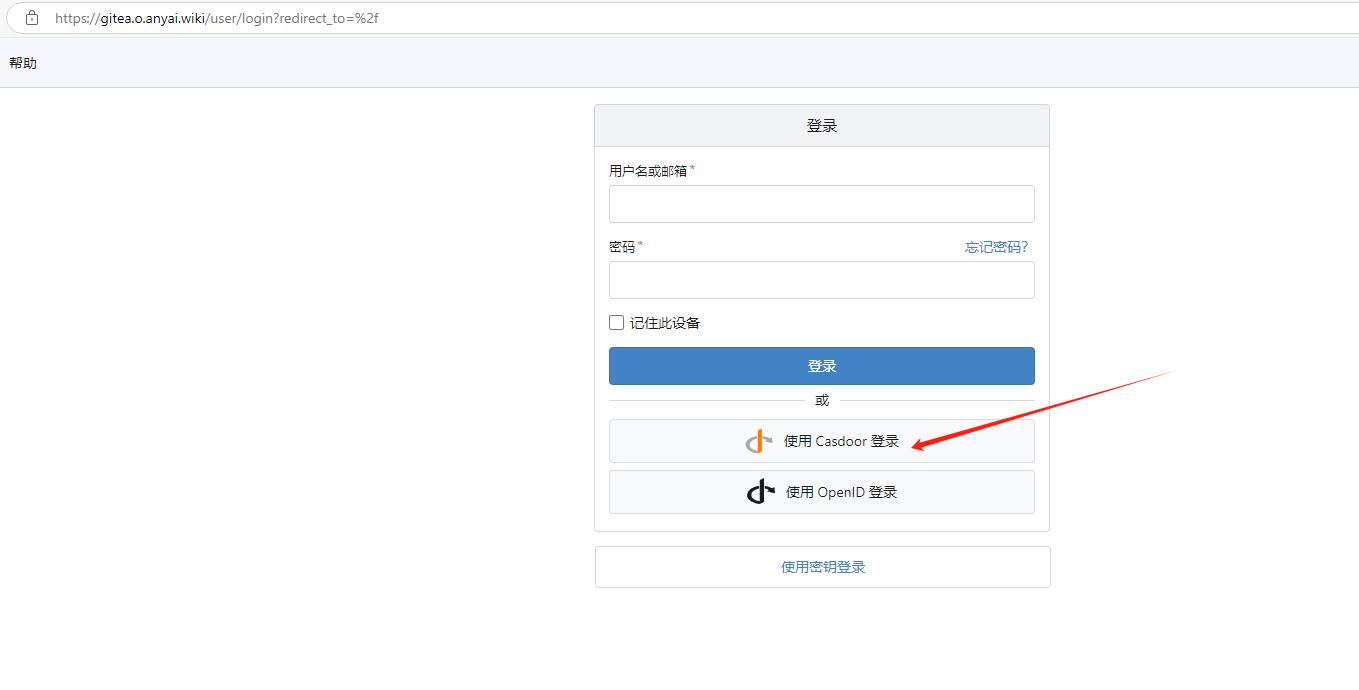
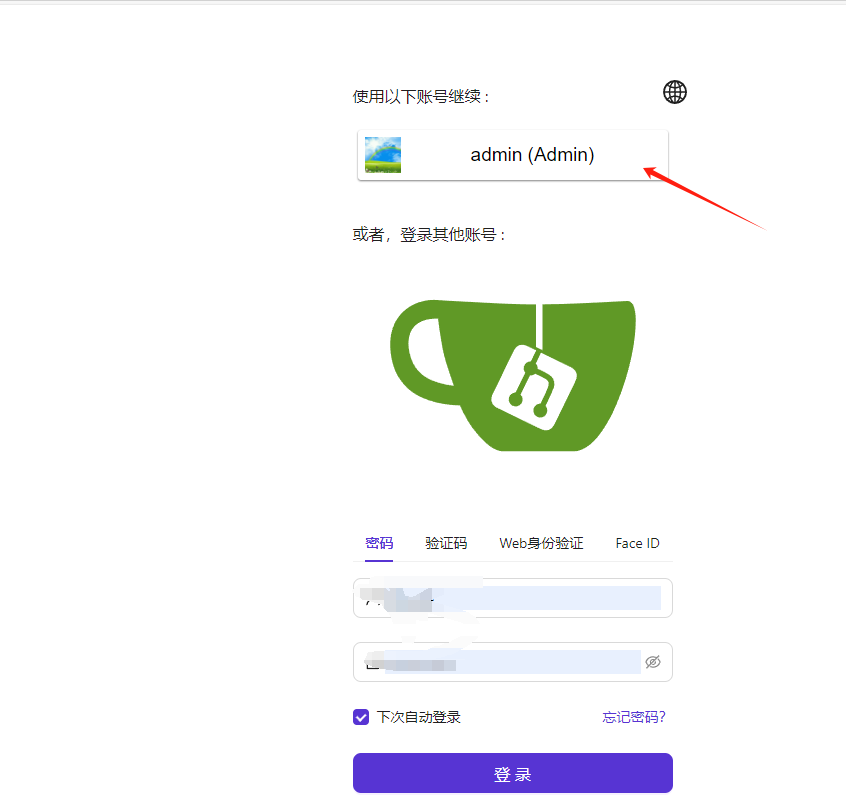
Clicking it will redirect to the unified login page, where you can choose the logged-in account or log in again.
You can design separate login redirect pages for each application.
Configuring Harbor
Go to Casdoor to configure the application.

Then configure OpenID in Harbor, but the Endpoint does not need to include the suffix `/.well-known/openid-configuration`.
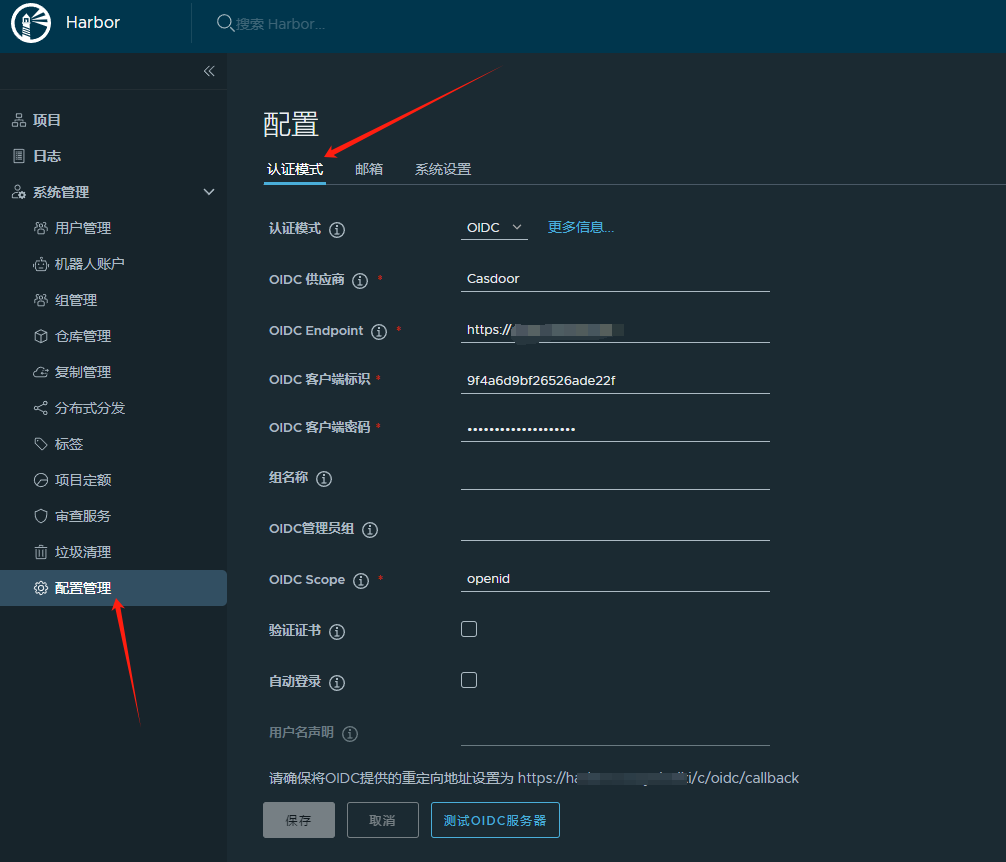
Harbor's configuration may have pitfalls. If the displayed callback URL is different from the current Harbor access address, you may need to configure the reverse proxy address in Harbor. Refer to:
https://www.whuanle.cn/archives/21744

文章评论